[Updated 7/11/2019 – Azure AD now supports FIDO2 tokens for MFA, which also protect against EvilGinx2]
This is my second blog post in this series. In the first blog post (here) Aidan Holland (@thehappydinoa) demonstrated how EvilGinx2 can bypass Microsoft’s 2FA that is built into Office 365 (SMS Text or Mobile Authenticator), sometimes called “Always-On MFA.”
Kuba Gretzky (@mrgretzky) stated that it can defeat any form of 2FA!
“Be aware that: Every sign-in page, requiring the user to provide their password, with any form of 2FA implemented, can be phished using this technique!” https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens
That’s a bold claim! Matt Soseman from Microsoft says, “always combine MFA with Conditional Access.” Matt is one of Microsoft’s top Cybersecurity experts, as he spoke on behalf of Microsoft at the RSA Security Conference in March 2019 (PDF HERE).
In this blog post, we are going to put both claims to the test. How does Microsoft’s Conditional Access compare against Evilginx2? We tested 13 of Microsoft’s defense capabilities and found 7 ways to defeat EvilGinx2. We also provide 4 recommendations for Microsoft to further improve security, and 5 recommendations for customers.
First, let’s define terms.
- 2FA, or ‘two-factor authentication’ is most commonly something you know like a password, and then some other factor like an SMS text code or a token-based Authenticator mobile app.
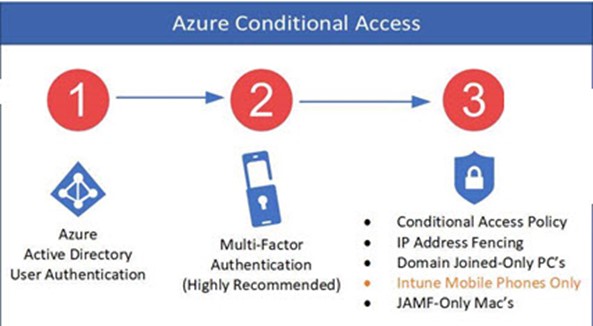
- MFA, or ‘multi-factor authentication’ can be multiple factors, not just two. For example, Microsoft’s conditional access allows you to go beyond user-authentication to perform machine authentication. You can check to see whether a computer is joined to the on-premises Active Directory domain, or whether it has a certificate issued from Active Directory Certificate Services (using Microsoft Cloud App Security Conditional Access App Control), or is originating from a range of IP addresses (aka IP-fencing). You can also check for the risk level of a user identity (using Azure Identity Protection) or the risk level of a machine (with Microsoft Defender ATP).
In our testing, we found that while EvilGinx2 is successful in bypassing the user-authentication forms of 2FA (yes, even the Microsoft Authenticator App!), and Azure Identity Protection.
EvilGinx2 was unsuccessful in bypassing the full MFA capabilities that Microsoft offers in Azure Conditional Access. This is available for customers who own the Azure AD Premium P1 license, which is also bundled in Enterprise Mobility Suite E3, and/or M365 E3.
Anyone who owns Azure AD Conditional Access can protect themselves from EvilGinx2 MFA bypass. Anyone who does not own Conditional Access can partially defend themselves against EvilGinx. The client access rule only protects Exchange Online, not SharePoint Online, OneDrive, Dynamics, or any of the other Office 365 or Azure services.
How does EvilGinx2 Work?
In order to understand how Azure Conditional Access can block EvilGinx2, its important to understand how EvilGinx2 works. First, the attacker must purchase a domain name, like “office-mfa.com” and convince an end-user to click on that link. The attacker’s machine passes all traffic on to the actual Microsoft Office 365 sign-on page. Since all traffic is passed directly through, the end-user sees the *actual* Office 365 sign-in page. This means the attacker does not have to waste valuable time trying to make the page look identical. The authentication token is captured after the user performs user-based authentication (SMS or Authenticator App). The attacker can then import the cookie into their own browser to access Office 365. In our testing, the link was not blocked by MSFT EOP, Office ATP, Microsoft Defender ATP, or Windows Defender SmartScreen. However, we did find at least three methods that blocked EvilGinx2.

Figure 1 image credit – breakdev.org
The attacker’s EvilGinx2 server terminates the SSL session and it then re-transmits a new SSL session against login.microsoftonline.com. This avoids all SSL errors in the browser, since there is a valid ssl handshake to the attacker’s machine. This is an advantage for the hacker, but it turns out to be the Achilles heel because Azure Conditional Access can perform additional checks that will all block EvilGinx such as: IP address, Domain Join Membership, Compliance (via Intune UEM), or Certificate (via CASB).
Here is a screen shot showing Azure Conditional Access blocking EvilGinx2 because the attacker’s IP address does not match the policy.
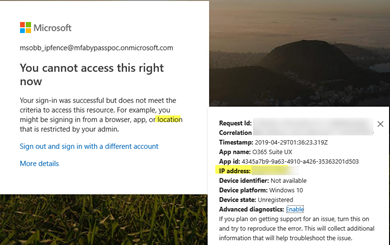
Here is a screen shot showing that Azure Conditional Access blocks EvilGinx2 because the attacker’s proxy machine is not a domain-joined device
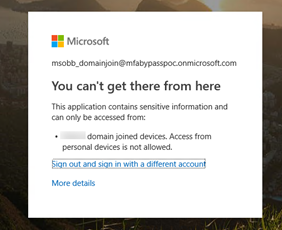
Here is a screen shot showing that Azure Conditional Access blocks EvilGinx2 because the attacker’s proxy machine is not meeting Intune compliance policy.
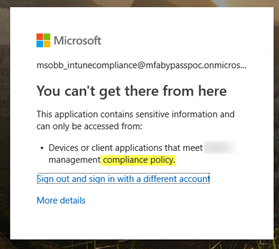
Here is a screen shot showing Microsoft Cloud App Security Conditional Access App Control successfully blocked the attacker from getting into Exchange Online because the attacker could not present a valid certificate.

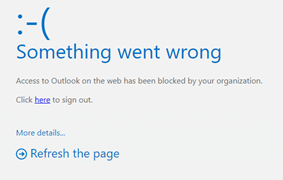
Here is a screen shot showing new-clientaccessrule blocking EvilGinx2 from accessing the mailbox in Office 365
Another method that blocks EvilGinx is U2F (Universal 2nd Factor Authentication). The author of EvilGinx2 states (here) that U2F “leaves no room for error and is totally unphishable using Evilginx method…” and that “make your life easier and get a U2F device! This will greatly improve your accounts’ security.” [Update: On July 10th, Microsoft formally announced that Azure AD now supports FIDO2 in public preview (read announcement here).]
So here is a summary of all known/possible defenses in Microsoft’s security arsenal and how they measure up against EvilGinx2.
| Defense | EvilGinx2 | Microsoft License Required | Notes |
| Always-On MFA: “SMS” aka Text Messaging | Bypass Successful | Any O365 Plan | The National Institute of Standards and Technology (NIST) updated guidance back in July of 2016 that government agencies should avoid SMS (NIST 800-63B).
There are several ways to bypass this form of 2FA (sim swapping, SS7, porting, etc). The Payment Card Industry (PCI) follows the NIST guidance in its latest supplement on MFA issued in July 2017. |
| Always-On MFA: “Authenticator App” | Bypass Successful | Any O365 Plan | Then authenticator app is much more secure than SMS/Text 2FA, however, because EvilGinx2 captures the authentication token issued, it successfully defeats even this more secure version of 2FA. |
| Azure Identity Protection | Bypass Successful
[Evilginx2 bypassed Azure Identity Protection] |
AAD P2 or (EMS E5, M365 E5, Identity & Threat Protection Bundle) | We enabled the user risk policy and the sign-in risk policy to block logins with any user risk. We assume that since we had the captured token, Azure Identity Protection is not continuously checking the user identity (unlike the new-clientaccess rule which checks every attempt). |
| Azure Conditional Access: IP Fence | Bypass Unsuccessful
[EvilGinx2 Blocked] |
AAD P1 or one of the bundles (EMS E3+ or MS365 E3+) | The reason why AAD Conditional Access can block EvilGinx is because the Attacker’s IP address is what is presented rather than the original user’s IP address. |
| Exchange Online Client Access Rule* (new-clientaccessrule) |
Bypass Unsuccessful against Exchange Online
[EvilGinx2 Blocked] |
Any Exchange Online License | Effective for protecting Exchange Online only.
(The hacker can get to office.com but then they get an error as soon as they click on Outlook) |
| Device Enrollment into Intune or Windows 10 Compliance Checking | Bypass Unsuccessful
[EvilGinx2 Blocked] |
Intune or EMS E3 or M365 E3 | Since the attacker’s machine is not enrolled into Intune, it cannot pass a compliance check and it is therefore blocked. |
| Certificate Based Authentication (Microsoft Cloud App Security Conditional Access App Control) |
Bypass Unsuccessful
[EvilGinx2 Blocked] |
AAD P1 + Microsoft Cloud App Security (or EMS E5) | The attacker can get to office.com but then they get an error as soon as they access an application protected by an MCAS CAAP access policy) |
| Hybrid Domain Join | Bypass Unsuccessful
[EvilGinx2 Blocked] |
AAD P1 or EMS E3 or M365 E3 | The reason why AAD Conditional Access can block EvilGinx is because the Attacker’s proxy device is presented rather than the original user’s device |
| Custom Branding | Bypass Unsuccessful
[EvilGinx2 Blocked] |
AAD P1 or EMS E3 or M365 E3 | Note: in our testing, the ‘custom branding’ feature in AAD P1 caused EvilGinx2 to not render the sign-in page (this is a problem that they should be able to fix though, so I wouldn’t depend on this as a permanent countermeasure). |
| U2F (Ex: Yubico) | Bypass Unsuccessful
[EvilGinx2 Blocked] |
AAD P1 or EMS E3 or M365 E3 | The author of EvilGinx has already tested and confirmed that U2F will successfully block because of the U2F origin binding implementation. |
| Windows Defender Smart Screen | Smart Screen does not block an EvilGinx hyperlink
(due to zero reputation) |
N/A – built into Internet Explorer since version 7, and Microsoft Edge and Windows 10 Creators Update, and available as an add-on for Chrome | Smart Screen seems to only be effective against URLs that are in a block list. Since hyperlinks generated by EvilGinx have zero reputation, they are not blocked by Smart Screen. |
| Exchange Online Protection and/or Office 365 Advanced Threat Protection | EOP and/or ATP does not block an EvilGinx hyperlink (due to zero reputation) | Office 365 E5 or M365 E5 | Since hyperlinks generated by EvilGinx have zero reputation, they are not blocked by ATP Safe Links. Safe Links records that the link was clicked on, which can be searched later using the URL trace feature. |
| Microsoft Advanced Threat Protection (prior to March 21st 2019 it was called Windows Defender ATP) | MDATP (aka WDATP) does not block EvilGinx | Windows 10 E5 or M365 E5 | Microsoft ATP records that the link was clicked on but it does not block it. |
Recommendations for Office 365 Customers
- If you are an Office 365 E3 subscriber, upgrade to Enterprise Mobility Suite and configure Azure AD Conditional Access for either (machine-authentication (domain-join checking, certificate checking) or IP address fencing) or (compliant device checking with Intune for Mobile Devices or Intune UEM for Windows 10). If you need assistance, find a qualified Microsoft Partner (here) and scroll down to the bottom.
- Consider implementing client access rules to protect Exchange Online. For an excellent overview of how client access rules work, watch this MSFT Ignite Video (here), fast-forward to 7:35 and watch until 15:55. Here is an example client access rule targeting a test account.
new-ClientAccessRule -name “Allow InternalIP Only” -Action DenyAccess -ExceptAnyOfClientIPAddressesOrRanges [enter your public IP addresses here] -UsernameMatchesAnyOfPatterns *TestUserName
-
Plan a U2F deployment, for example with Yubico. [This is now supported with Azure AD as of 7/10/2019].
“With the YubiKey, user login is bound to the origin, meaning that only the real site can authenticate with the key. The authentication will fail on the fake site even if the user was fooled into thinking it was real. This greatly mitigates against the increasing volume and sophistication of phishing attacks and stops account takeovers.” Reference https://www.yubico.com/solutions/fido-u2f/
- Perform regular Security Awareness training to help users recognize suspicious URLs.
Note: Microsoft’s Office 365 ATP has an exclusive feature called ‘Native Link Rendering’
to show users the original hyperlink when they hover over it. No other advanced hyperlink scanning solution has this capability (I asked all the top vendors this question including ProofPoint, Mimecast, FireEye, Symantec and others). Native Link Rendering requires the Office 365 C2R (click-to-run) version, and not the volume-licensed MSI installer version of Office. Monthly Channel 1808 release (September 2018) or Semi-Annual Channel 1901 (which has not rolled out yet except to the Semi-Annual Targeted channel). See release notes (here). - Harden the Office 365 tenant. A good place to start is my blog post ’20 Things to do before and after a phishing event in Office 365′. And we also offer a monthly service to continuously audit and harden Office 365, for more on that service click here.
If you are investigating an incident and you believe a user’s token has been captured, you can invalidate a token with this AAD PowerShell cmdlet
$date =get-date; Set-Msoluser -UserPrincipalName (UPN) -StsRefreshTokensValidFrom $date
Feedback for Microsoft:
- Microsoft should consider improving Office ATP Safe Links and/or SmartScreen to take into consideration the age of a newly registered domain name. Some of Microsoft’s competitors can check the age of a domain name when determining hyperlink reputation.
- Microsoft should consider developing features similar to new-clientaccessrule for the other services in Office 365 like SharePoint Online, OneDrive for Business, Teams, Dynamics
- Azure Identity Protection could be improved to check every attempt, similar to new-clientaccesrule. We assume the fact that we had imported a captured token is why we did not get triggered by the User Risk policy or Sign-in risk policies (which were both set to ‘low and above’ with the block control).
-
Don’t give away which factor of authentication was the reason why the attacker could not sign-in. For example, in our testing the attacker is able to learn whether it was a domain join check or a compliance check that they failed. This is precisely what the PCI DSS takes issue with in their MFA guidance (here)

Therefore we recommend that Microsoft change from Multi-Step to true Multi-Factor authentication. Today, any world-wide user can attempt to guess a username and password, only to then be blocked by a subsequent policy. This arms the attacker with too much information on which challenge failed.
-Joe Stocker, CEO
Patriot Consulting Technology Group, LLC
Our Mission “to empower our clients to manage cyber security risk by securely deploying Microsoft Cloud technology”


