“Complexity is the worst enemy of security, and our systems are getting more complex all the time.” – Bruce Schneier (@schneierblog)
Microsoft recently launched “Authentication Methods Policy Convergence” (Public Preview). This is so very exciting because it exponentially reduces the complexity of multifactor authentication. I was part of the private preview program, and I’m very happy to see this feature going public.
In my book, “Securing Microsoft 365 (2nd Edition) (2022)” I write about the imperative of Zero Trust and how to configure multiple factors of authentication to prevent unauthorized access to Microsoft 365. Three years ago, I wrote about the most common MFA myths and misconfigurations that I have seen in customer environments.
As of the fall of 2022, only 25% of all authentications are protected by MFA in Microsoft Entra (Azure Active Directory). So this new simplified experience of configuring MFA is such an incredibly welcome improvement. I believe we will see a significant improvement in MFA adoption over the next two years. The reason it will take some time is because the policy convergence is not yet a forced experience, meaning we will still see customers configuring MFA in multiple portals until they learn about policy convergence. And that is why I am writing this blog article, to get the word out! In January 2024, the legacy multifactor authentication methods portal and SSPR authentication methods will be deprecated. Until then, it is very important to note that the new Authentication methods are evaluated in addition to the legacy MFA and SSPR policies.
One of the biggest improvements that I like about policy convergence is that not only do we get a single place to configure MFA authentication methods, but we also get the ability to target individuals and groups. Previously, if you wanted some users to have the ability to use SMS/TEXT or Voice then you had to enable it for the entire tenant. With policy convergence, we now have the ability to be more selective!
You can migrate your existing policies to the new blade at your own pace. Make sure to follow the latest Microsoft Documentation: “Migrate MFA and SSPR policy settings to the Authentication methods policy for Azure AD” and “ Manage authentication methods for Azure AD”
Support for Hardware OATH tokens and Security Questions is coming soon. If you’re using hardware OATH tokens or Security Questions (for SSPR), do not proceed further.
After you capture available authentication methods from the policies you’re currently using, you can start the migration.Open the Authentication methods policy, click Manage migration, and click Migration in progress. You’ll want to set this option before you make any changes as it will apply your new policy to both sign-in and password reset scenarios.
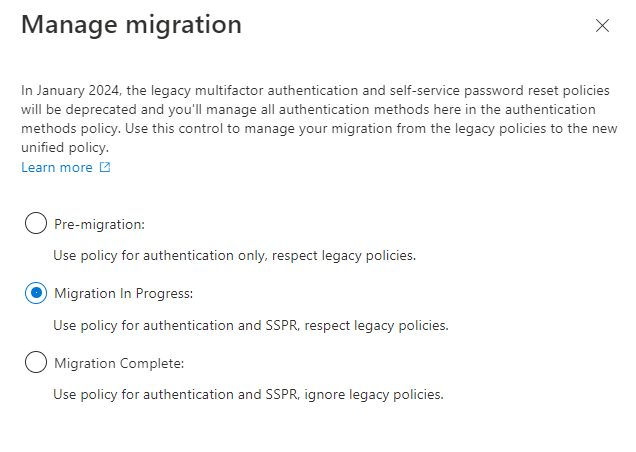
Then, update the new auth methods to match the methods you are currently using, or take this as an opportunity to eliminate the less secure methods. If you do that, just be aware that the user will be forced to register for the more secure methods at their next sign-in (so it would be wise to inform your helpdesk and send an email to your users about what they are going to expect!).
After you update the Authentication methods policy, go through the legacy MFA and SSPR policies and remove each authentication method one-by-one. Test and validate the changes for each method. Then go back to the migration process and mark the migration as complete.
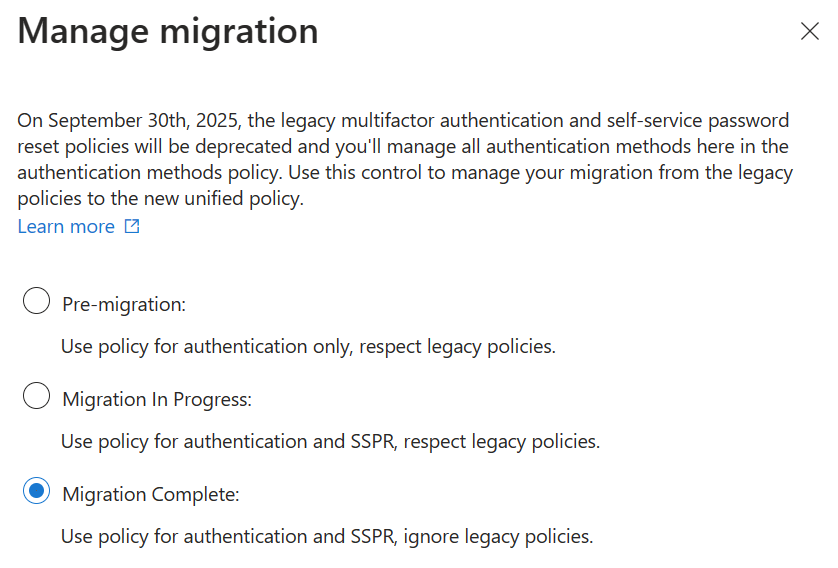
Be aware that it can take up to 15 minutes before changes are reflected.
After reviewing Jan Bakker’s (@janbakker_) blog post on this same subject, I realized that I could not improve upon it any further, so I just want to direct my readers there because he did such a good job on describing the experience in such great detail: https://janbakker.tech/goodbye-legacy-sspr-and-mfa-settings-hello-authentication-methods-policies/
For example, Jan points out “Ensure you have also enabled the combined registration portal for SSPR and MFA before using the new policies. Microsoft should have already enabled this feature, starting Sept. 30th, 2022, but I still see tenants where this is disabled.” I too have seen customers with that disabled, so here is the setting that Jan shared on his post:

