I consider myself an early adopter of most Microsoft security controls, not just to protect our own organization, but with the goal to help the community understand the potential benefits and impacts of various configuration options.
After I enabled the new Entra Conditional Access “Authentication Flows” block policy, my mobile phone could no longer sign into the Outlook for iOS or Teams mobile applications.
The error message I received was “You don’t have access to this. Your sign-in was successful but does not meet the criteria to access this resource. For example, you might be signing in from a browser, app, location, or an authentication flow that is restricted by your admin.”
That’ when I knew that the change I had rolled out about 6 hours earlier was probably the culprit. I immediately reported the findings to Microsoft and began working with the product group to identify the root cause. Essentially, the behavior is expected if the mobile phone apps were registered using one of these flows.
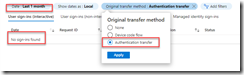
Device code flow is required when signing into devices that might lack local input for eg meeting room devices or scenarios like shared devices. But in some cases, mobile phones can use these flows to register apps like Authenticator in Passwordless mode.
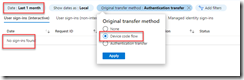
My recommendation is to enable this policy in ‘Report Only Mode’ OR review the past sign-ins to see if these events have been happening in your environment.
In the Entra Sign-in logs you can now filter for authentication flows to see if which users are signing in with these flows.
The quick fix would be to exclude the users who may be affected. In my organization, it was just one user who was impacted. If you want to get more granular on the exclusion, exempt only the specific device ID’s from the DCF CA policy and then create a second standalone “require compliant device” for those specific device ID’s (assuming they are corporate owned devices). Essentially, whenever there’s a “require compliant device” policy in place, DCF is automatically blocked. This is because MSFT cannot verify the registration state of devices as part of the DCF flow. Thus, a managed device pass the compliant device requirement but any further DCF attempts should be blocked for that specific device. For unmanaged BYOD devices, then you normally can’t use the “require compliant device” policy since that would require full MDM device enrollment (most organizations with BYOD policies cannot or do not want to fully manage a personal device).
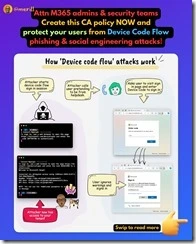
Merill Fernando (@Merill) posted on his X account a helpful diagram on why blocking Device Code Flow is important.
References:
Microsoft Documentation: https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-authentication-flows
Dirk-jan Mollema (@dirkjan) https://dirkjanm.io/phishing-for-microsoft-entra-primary-refresh-tokens/
@fabian_bader’s blog post https://cloudbrothers.info/en/protect-users-device-code-flow-abuse/