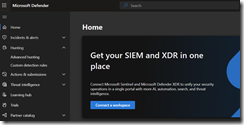
On April 3rd, 2024, Microsoft’s new Unified Portal became public preview, where anyone running their Sentinel SIEM can connect it to the Microsoft Defender XDR Portal (Security.Microsoft.com).
My thought is that you would want this because Copilot for Security would be more helpful, and also it reduces the inevitable pivot that must occur when you start off in Sentinel and then have to switch to the Defender XDR Portal to perform a deeper investigation, say for example within MDE Timeline, or an MDO Email Investigation.
Unify the two portals into one!
The first step is to browse to the Defender XDR Portal and then click “Connect a workspace”
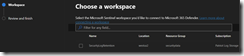
You should then see the Log Analytics Workspace to connect.
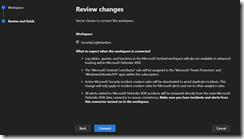
The last step is to click the Connect Button.
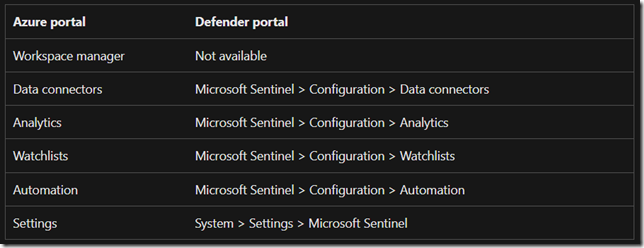
What to expect when the workspace is connected
- Log tables, queries, and functions in the Microsoft Sentinel workspace will also be available in advanced hunting within Microsoft Defender XDR.
- The ‘Microsoft Sentinel Contributor’ role will be assigned to the ‘Microsoft Threat Protection’ and ‘WindowsDefenderATP’ apps within the subscription.
- Active Microsoft Security incident creation rules will be deactivated to avoid duplicate incidents. This change will only apply to incident creation rules for Microsoft alerts and not to other analytics rules.
- All alerts related to Microsoft Defender XDR products will be streamed directly from the main Microsoft Defender XDR data connector to ensure consistency. Make sure you have incidents and alerts from this connector turned on in the workspace.
What I observed in my Sentinel instance is the incident creation rules were not deactivated. They were still enabled.
What concerned me the most was the deactivation of the Security Incident Creation Rules. Even though it sounds good on the surface to avoid duplicate incidents, the concern I had is for customers who have an MSSP monitoring their Sentinel Instance, as this would cut off their visibility into those incidents, unless the MSSP somehow transitions to using the Unified Portal, which is not scalable (yet) to allow a SOC analyst to triage multiple incidents in the same view.
“Alerts and incidents from Microsoft Defender XDR (those items which populate the SecurityAlert and SecurityIncident tables) are ingested into and synchronized with Microsoft Sentinel at no charge. For all other data types from individual Defender components (such as DeviceInfo, DeviceFileEvents, EmailEvents, and so on), ingestion will be charged.
Once the Microsoft Defender XDR integration is connected, the connectors for all the integrated components and services (Defender for Endpoint, Defender for Identity, Defender for Office 365, Defender for Cloud Apps, Microsoft Entra ID Protection) will be automatically connected in the background if they weren’t already. If any component licenses were purchased after Microsoft Defender XDR was connected, the alerts and incidents from the new product will still flow to Microsoft Sentinel with no additional configuration or charge”
Reference: https://learn.microsoft.com/en-us/azure/sentinel/microsoft-365-defender-sentinel-integration#connecting-to-microsoft-defender-xdr
So far based on our testing, the alerts from Defender are still visible by Lighthouse, so testing helped alleviate this concern.
Table Synchronization
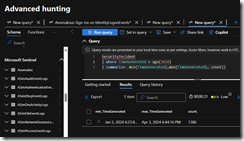
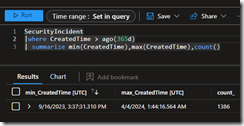
My first test was to see if the synchronization of the SentinelIncident table is limited by the 30 day KQL History of the Advanced Hunting experience.
The first screenshot is from the Defender XDR Portal and the second screenshot is from Sentinel. You’ll observe the data is identical, and I was able to use the same KQL query:
SecurityIncident
| where CreatedTime > ago(365d)
| summarize min(CreatedTime),max(CreatedTime), count()
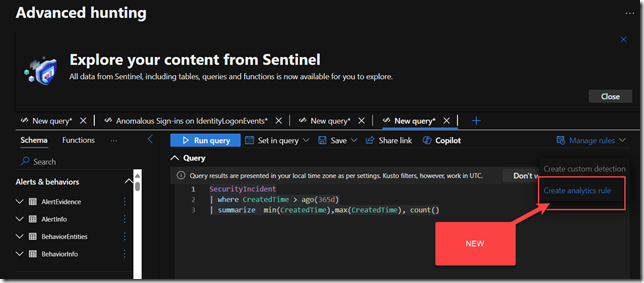
You can also create Analytics Rules from within the Defender Advanced Hunting interface:
The components that are now “Unified” between Defender and Sentinel are:
- Overview
- Unified Incidents
- Unified Entities
- Advanced Hunting
Key benefits are summarized in the Microsoft Documentation (here).
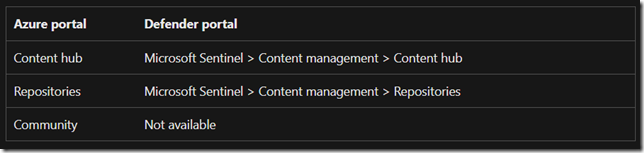
The following capabilities are only in the Sentinel Portal:
- Tasks
- Adding an entity to threat indicators
- Automation
- Workspace Manager
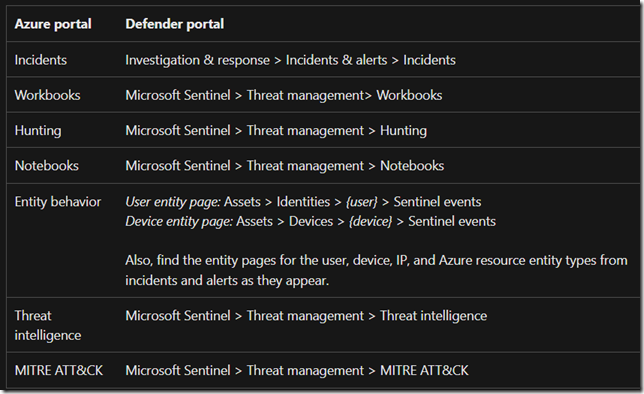
Otherwise the Documentation page does a great job at mapping where to find Sentinel features inside the new Unified Portal:
Uninstalling (Roll Back)
This is possible in the Defender XDR Portal by disconnecting the Workspace. It is not clear to me whether you would have to re-enable the Defender Incident Creation rules in Sentinel.
Final Thoughts
The expanded Advanced Hunting experience and being able to stay within a single console without having to bounce back and forth between Sentinel and Defender makes this a compelling integration. My initial concern about impact to MSSP’s was alleviated by testing in our own Azure Lighthouse environment.