MailItemsAccessed is a new audit event in Office 365 that records when email data is accessed by mail protocols and clients.
Why is MailItemsAccessed so important?
During an investigation where a mailbox has been accessed by an unauthorized party, there are often legal requirements (State, Federal and Global Treaties such as GDPR) to notify individuals if their personally identifiable information was accessed. Without MailItemsAccessed we could only say that the attacker had the capability of accessing all mailbox contents, but we couldn’t say which exact emails were accessed. The sync event is still not as definitive as we would like, but it does show that the attacker now has possession of the mailbox contents. If the attacker accessed the mailbox via a web browser, then it’s helpful to know which individual items were accessed.
If a privileged account was compromised, it’s also a good idea to check whether the attacker enabled the Bypass audit log PowerShell command to cover their tracks.
For more details, see Access to crucial events for investigations.
How does MailItemsAccessed compare to MessageBind?
MailItemsAccessed replaces the audit event ‘MessageBind’ which was deprecated in Exchange Online on 1/23/2019. This audit event began rolling out in Q1 2020 after a 12 month pause from the first announcement in January 2019. Tony Redmond has documented the history of this rollout on his blog, with his latest post on March 6, 2020 (here).
MessageBind was only available for the AuditAdmin user logon type and did not record actions performed by the Mailbox Owner or Delegate. MessageBind only covered actions by a mail client and did not record sync activities. MessageBind also generated multiple audit records for the same email message. MailItemsAccessed fixes all these deficiencies.
– MailItemsAccessed applies to all logon types (Owner, Admin and Delegate)
– MailItemsAccessed applies to both an individual email being read in addition to a ‘sync’ event such as MAPI, POP or IMAP downloading all email in a client.
– MailItemsAccessed aggregates multiple events into fewer audit records.
Licensing
Office E5 or (M365 E3 + “E5 Compliance” add-on)
One question that is often asked is: “If I buy just one license, does this enable the capability for all users.” The answer is no. Only users with the appropriate license will have the MailItemsAccessed logged.
Deployment
MailItemsAccessed is only enabled by default when the E5 feature “Microsoft 365 Advanced Auditing” license has been applied to the account.
(In PowerShell the auditing license will appear as “M365_ADVANCED_AUDITING”).
To find out how many of your current mailboxes are logging the MailItemsAccessed event run this Exchange Online PowerShell command:
get-mailbox -ResultSize unlimited | where {$_.AuditOwner -like ‘*Accessed*’}
Note: See troubleshooting section if you have the right license and MailItemsAccessed is still not appearing.
Prior to 2/1/2019, Mailbox Owner auditing only logged a single event by default: MailboxLogin. After 2/1/2019, additional events were added unless auditing had been customized. If you customized the mailbox actions to audit for any logon type before mailbox auditing on by default was enabled in your organization, the customized settings are preserved on the mailbox and aren’t overwritten by the default mailbox actions that were since added. The exception to this rule seems to be with MailItemsAccessed because it was appended to the E5 mailboxes that had been set to use customized audit events.
To reset auditing to defaults you can run use the DefaultAuditSet parameter, which is generally recommended because according to the documentation “Any new mailbox actions that are released by Microsoft are automatically added to the list of audited actions for the logon type.”
Set-Mailbox -Identity (mailbox identity) –DefaultAuditSet Admin,Delegate,Owner
If you want to find out the mailboxes that have the default auditing enabled, run this command and look for “Admin, Delegate, Owner.” The absence of one of these means that audit customizations was applied to that mailbox.
get-mailbox | select name,DefaultAuditSet
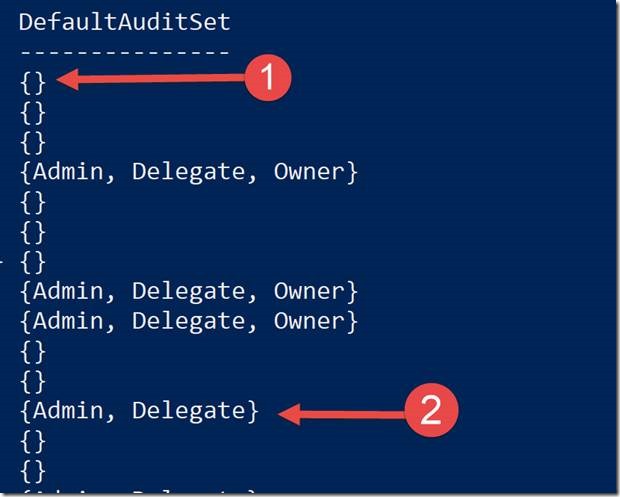
For example, in the screen shot above (1) means that all three roles were customized and (2) means only the Owner was customized because it is absent from the list.
Note: DefaultAuditSet does not audit all possible audit events. It will audit the following seven events (or eight when an E5 license is applied to the mailbox)
1. Update
2. MoveToDeletedItems
3. SoftDelete
4. HardDelete
5. UpdateFolderPermissions
6. UpdateInboxRules
7. UpdateCalendarDelegation
8. MailItemsAccessed (<- THIS IS ONLY ADDED IF AN E5 License is applied to the mailbox)
For a list of the defaults see the documentation (here).
The following three events can be added as additional audit events for the Owner logon type:
1. Create
2. MailboxLogin
3. Move
Therefore, to apply all 11 possible audit events, run this command:
get-mailbox -ResultSize unlimited | set-mailbox -AuditOwner @{Add= “Update”,”MoveToDeletedItems”,”SoftDelete”,”HardDelete”,”UpdateFolderPermissions”,”UpdateInboxRules”,”UpdateCalendarDelegation”,”Create”,”MailboxLogin”,”Move”,”MailItemsAccessed”}
Repeat above command and swap out AuditOwner for AuditDelegate and AuditAdmin but remember to check the table (here) because not all audit events are available for Admin
Note: A user with full mailbox access to another user’s mailbox is logged as AuditDelegate.
Searching Audit Events
You can search for MailItemsAccessed events in Protection.office.com

Compliance.microsoft.com will eventually replace Protection.office.com.

You can also use Exchange Online PowerShell to search for audit events, which is required if you need to search for events older than 90 days. Search-UnifiedAuditLog -Operations MailItemsAccessed or Search-MailboxAuditLog -Operations MailItemsAccessed
Other useful Exchange Online PowerShell commands:
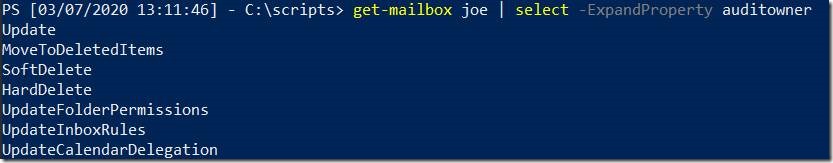
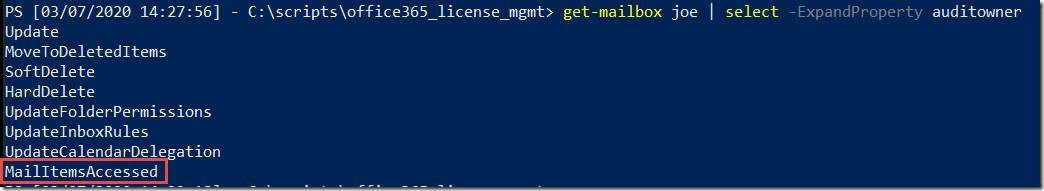
View which events are being logged on a single mailbox (“Joe”)
get-mailbox joe | select -ExpandProperty auditadmin
get-mailbox joe | select -ExpandProperty auditowner
get-mailbox joe | select -ExpandProperty auditdelegate
Report how many accounts have auditing enabled:
get-mailbox | group-object AuditEnabled
Enable auditing on all mailboxes and increase audit log retention from 90 days to 180 days:
get-mailbox -resultsize unlimited | set-mailbox -AuditEnabled $true -AuditLogAgeLimit 180
Audit Log retention is independent of whether or not a retention policy (aka Legal hold) is applied to the mailbox. For example, if a mailbox is under legal hold, the audit events are not retained longer than the duration set by the AuditLogAgeLimit parameter.
If you increase the age beyond 90 days, you can only find those items in PowerShell using Search-MailboxAuditLog.
The following capacity limitations apply to mailbox auditing:
– No more than 3 million audit records are allowed per mailbox
– No more than 30 GB of audit records are allowed per mailbox (100GB if legal hold or retention policy has been applied to the mailbox)
– Tony also states in his blog “Exchange Online applies throttling for MailItemsAccessed events. If a mailbox generates more than 1,000 bind events in a 24-hour period, Exchange Online stops recording MailItemsAccessed events for bind operations for another 24 hours before resuming capture of these events. Microsoft says that less than 1% of mailboxes are subject to throttling.”
Troubleshooting
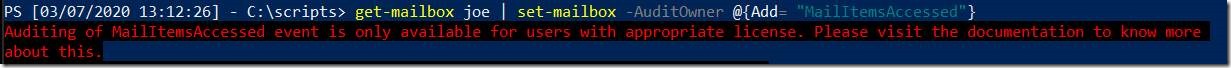
Assume you have a mailbox where MailItemsAccessed is not applied, but the mailbox has an E5 license.
You then try to add the audit event but you get an error that its only available for users with the appropriate license.
Double-check to see that you have the “Microsoft 365 Advanced Auditing” license type assigned.
Note: In my case, even though the box was checked, it did not work because this license assignment was inherited from an Azure AD P1 feature called Group-based licensing. So to work-around this bug, I directly assigned the license via PowerShell (since I couldn’t via the GUI since the checkbox was already selected) and that allowed the MailItemsAccessed to be applied.
$MSOLSKU = “(tenantname):ENTERPRISEPREMIUM”
$myO365Sku1 = New-MsolLicenseOptions -AccountSkuId $MSOLSKU
Set-MsolUserLicense -UserPrincipalName (username) -LicenseOptions $myO365Sku1