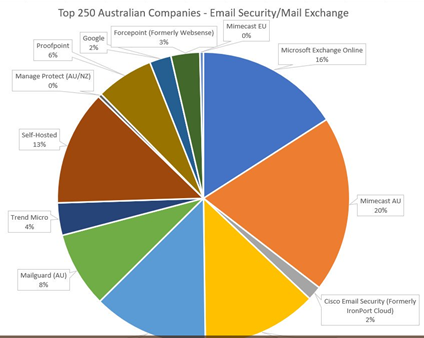
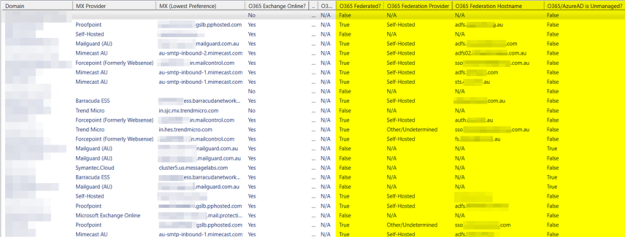
Statistics indicate that 20% to 50% of corporate users will give away their username and password when asked to do so by a social engineer (for example through a phishing email).
50% to 70% of corporate users admit to recycling their password across multiple websites. Users will memorize no more than 5 unique passwords, and then they start to increment numbers on the end. Then when these websites are hacked, the passwords can be put into credential stuffing tools like SNIPR to see what websites those passwords can be used on.
Some of the more clever and convincing phishing emails originate from a trusted person such as the CEO, HR Department, IT Department, or even Microsoft. The HR Department example might say “you have received an encrypted message from HR” and if you click on the link to view the message, it steals your O365 password. The attacker then logs into your account, forwards your email to them, and then send emails out to your customers or other colleagues to continue to propagate.
Here are a few tips on how to prepare for when this happens to you.
- Be prepared to Reset the affected user’s password right away. Note that if you reset the password on-premises, it can take a few minutes before that password change is synced to Office 365 (if you are using Password Hash Sync, it can take 3 to 4 minutes). If you are using ADFS or AAD PTA then there is no delay.
- Document the steps to revoke an active user’s session in Office 365, forcing them to try to logon with the new password. There are five supported methods, but in my testing I get mixed results on how quickly they take effect. For example, on a mobile device that previously authenticated with an MFA token for ActiveSync, none of the below methods seem to immediately invalidate the MFA token. Fortunately, most account takeovers in O365 are browser-based, so this shouldn’t be a problem to proceed with any of the options below.
Option 1) Reset the user’s password. This will invalidate the current token.
Option 2) In Azure AD remote powershell:
$RefreshTokensValidFrom = Get-DateSet-MsolUser –UserPrincipalName <UPN of the User> –StsRefreshTokensValidFrom $RefreshTokensValidFrom
Note StsRefreshTokenValidFrom will appear to accept any date, but it will always set to the current date and time.
Option 3) [Only applies if the user uses OneDrive] From the Office 365 Admin Center under Home > Active Users. Select a user and expand the OneDrive Settings section for that user. Select “Initiate” to perform a one-time sign-out for that user that revokes active sessions across Office 365 services including Exchange Online.
Option 4) Force logoff during an active user session in Office 365 to use Revoke-SPOUserSession cmdlet from the SharePoint Online PowerShell Module. This method is helpful for automating security incident response flows or when there is a need to revoke multiple users’ sessions.
Option 5) Revoke-AzureADUserAllRefreshToken cmdlet is available in the AzureAD V2 PowerShell Module and expires a user’s refresh token by modifying the user’s token validity period”
Reference: https://blogs.technet.microsoft.com/educloud/2017/06/14/how-to-kill-an-active-user-session-in-office-365/
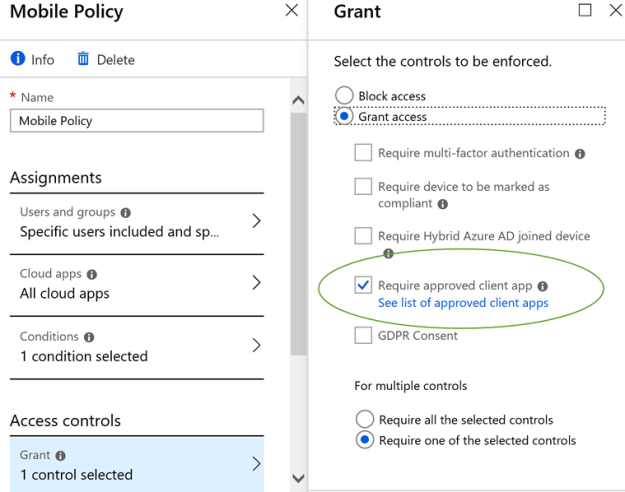
- Deploy Multi Factor Authentication on targeted users, privileged users, and users who access sensitive information. Many people do not know that O365 includes free MFA without the need for additional licenses.. it comes built into all O365 plans. Make sure you read the MFA Best Practices blog post here.
- Check to see if mailbox forwarding was enabled, and if so to who (document the external addresses to verify the validity).
Here is a great one-liner to run in Exchange Online Powershell:
get-mailbox -resultsize unlimited |where {$_.ForwardingSmtpAddress -ne $null} | select displayname,forwardingsmtpaddress
- Check message trace logs in Exchange Online Admin center (http://outlook.com/ecp) to see what items were sent to suspected unauthorized external accounts.
-
- Prior to January 1st, 2019, Mailbox Auditing was disabled by default in Exchange Online. Microsoft began enabling it but in early 2019 they paused the audit of a particular action that was formerly known as MessageBind (deprecated 1/23/2019) with the renamed event MailItemsAccessed event, which tells you which emails the owner, delegate or administrator may have accessed. Tony Redmond wrote (here) that the rollout of this action will resume October 2019, per Message Center “MC193448”. At Ignite 2019 conference, it was announced that MailItemsAccessed would be included in ‘Advanced Auditing’ which is an E5 licensed feature. As of February 6th 2020, our tenant still shows no signs of this feature even though we have E5 licenses.
-
Review Azure Reports on a frequent basis. Note that detailed reports are not available with Azure AD Free, and require Azure AD Premium P1.
-
Risky Sign-Ins
- Sign-ins from anonymous IP addresses
- Impossible travels to atypical locations
- Sign-ins from infected devices
- Users flagged for risk
- Azure Sign In Logs (Requires P1) at portal.azure.com
- Office 365 Audit Logs at protection.office.com or soon to be security.microsoft.com
- Use Message Trace to see who received emails from the attacker’s email address.
- Use ATP URL Trace to view who clicked on the hyperlink sent from the attacker.
- Purge the email with PowerShell for any user who has not yet clicked on the email sent from the attacker.
There are two ways of doing this, and one is significantly faster than the other.
Method #1 is the traditional method and uses Search-Mailbox like this:
Get-Mailbox -ResultSize unlimited | Search-Mailbox -SearchQuery {Subject:“Urgent Memo from CEO” And received:05/31/2018..06/01/2018} -DeleteContent -Force
Note: You have to be assigned the Mailbox Import Export management role to use the DeleteContent switch.
Tip: gather what would be deleted first with this command: Search-Mailbox -Identity [email protected] -TargetMailbox [email protected] -TargetFolder Case1234 -SearchQuery “Subject:Click Here to get a Virus”
Method #2 is newer and is a LOT faster.
Search in the compliance center, export the result for evaluation (optional), then proceed with connecting to Exchange Online remote PowerShell and running these two commands (replacing with the search name you used in the compliance center).
Get-ComplianceSearch -Identity “My Bad Virus”
New-ComplianceSearchAction -SearchName “My Bad Virus” -Purge -PurgeType SoftDelete
- Cloud App Security is valuable for many reasons, but it extends the auditing to 180 days whereas the built-in audit logs in the Office 365 Security and Compliance Center only go back 90 days.
Licensing: CAS is available in two forms, O365 E5 or EMS E5… the former protects mostly O365 and 750 other SaaS apps, whereas the later protects 15,000 SaaS apps and supports automatic log uploads from your on-premises firewalls.
- Office 365 Threat Intelligence (an E5 feature) can identify who your top targeted users are and alert you when there are active email campaigns going on so that you can alert your users of the threat.
- Consider Disabling User Consent to 3rd party applications in Azure Active Directory. This prevents users from granting consent to 3rd party apps that may be the next wave of ransomware, that encrypts mailboxes. There is a new capability that allows Admins to approve apps that users request. A proof of concept was recently demonstrated on the internet. Review existing oAuth grants.
- Deploy ATP Anti-Phishing. For more details: https://support.office.com/en-us/article/Set-up-Office-365-ATP-anti-phishing-policies-5a6f2d7f-d998-4f31-b4f5-f7cbf6f38578
- Disable Legacy Authentication (This will be turned off October 2020, so might as well do it now)
For more information on this, read the MFA Best Practices blog post here.
- Disable POP/IMAP for future mailboxes and current mailboxes
Examples:
#All Future Mailboxes
Get-CASMailboxPlan | set-CASMailboxPlan -ImapEnabled $false -PopEnabled $false
#All Existing Mailboxes:
get-casmailbox | set-casmailbox -imapenabled $false -PopEnabled $false
- Disable SMTP Auth at the global level or mailbox level. This prevents users from using this as a brute force vector.
#Global Level
Set-TransportConfig -SmtpClientAuthenticationDisabled $true
#Mailbox Level
Get-casmailbox -resultsize unlimited | Set-CASMailbox -SmtpClientAuthenticationDisabled $true
- Disable user’s powershell access in Exchange Online, ex:
get-user | set-user -RemotePowerShellEnabled $false
#Don’t lock yourself out – use the where clause to exclude your account.
- Check Inbox rules and Delegate access in Exchange Online. For example, get-inboxrule -mailbox [email protected]
Single User:
Get-InboxRule -Mailbox [email protected] | where {$_.redirectTo -ne $null} |select mailboxownerid,redirectto,description
Multiple Users:
get-mailbox -resultsize unlimited |%{Get-InboxRule -Mailbox $_.userprincipalname} | Where-Object {($_.ForwardTo -ne $null) -or ($_.ForwardAsAttachmentTo -ne $null) -or ($_.RedirectsTo -ne $null) |select mailboxownerid,redirectto,description |Export-Csv .\inboxrules.csv -NoTypeInformationNote: For large organizations, this script can sometimes timeout, so you may need to incorporate a counter logic like I created in this other script I published on the TechNet gallery (here).
** TBD: Repeat the command above for any rule content where the RSS Subscriptions folder is mentioned. Note: Microsoft’s Cloud App Security has a rule to detect for malicious inbox rules like this.
Here is the script to check for delegates:
https://github.com/OfficeDev/O365-InvestigationTooling/blob/master/DumpDelegatesandForwardingRules.ps1
Microsoft has a new report to show all SMTP and Inbox Forwards https://protection.office.com/reportv2?id=MailFlowForwarding&pivot=Name
Tips:
Exchange Online Mailbox Auditing 101
get-mailbox | group-object AuditEnabled
This command will give you a quick and high level picture of how many accounts have Auditing enabled.
get-mailbox -resultsize unlimited | set-mailbox -AuditEnabled $true -AuditLogAgeLimit 180
This command will enable mailbox auditing on all accounts and increase the default audit level from 90 to 180
The following commands will show you the default auditing settings on a single mailbox user “Joe”
get-mailbox joe | select -ExpandProperty auditadmin
get-mailbox joe | select -ExpandProperty auditowner
get-mailbox joe | select -ExpandProperty auditdelegate
Prior to 2/1/2019, The Mailbox Owner auditing only logs a single event by default: MailboxLogin. After 2/1/2019, additional events are logged unless this has been customized.
Therefore, to enable the maximum level of auditing that you can for a mailbox owner, here is the command:
get-mailbox -ResultSize unlimited | set-mailbox -AuditOwner @{Add=”create”,”HardDelete”,”MailboxLogin”,”Move”,”MoveToDeletedItems”,”SoftDelete”,”Update”,”UpdateFolderPermissions”,”UpdateInboxRules”, “UpdateCalendarDelegation”}
Similar commands can be run for AuditDelegate and AuditAdmin.
References:
https://support.office.com/en-us/article/enable-mailbox-auditing-in-office-365-aaca8987-5b62-458b-9882-c28476a66918#ID0EABAAA=Mailbox_auditing_actions
MFA Reporting
The MFA reporting in Office 365 is almost non-existent. You need to go to powershell to audit who has been enforced, enabled or is not yet enabled.
- Enabled (Means the user has been enabled but they have not yet completed MFA registration)
Get-MsolUser -All | where {$_.StrongAuthenticationRequirements.state -eq ‘Enabled’ } | Select-Object -Property UserPrincipalName,whencreated,islicensed,BlockCredential | export-csv enabled.csv -noTypeInformation
- Enforced (The user has completed MFA registration, so their account is not protected by MFA)
Get-MsolUser -All | where {$_.StrongAuthenticationRequirements.state -eq ‘Enforced’ } | Select-Object -Property UserPrincipalName,whencreated,islicensed,BlockCredential | export-csv enforced.csv -noTypeInformation
- Not Yet Enabled (These users have not yet been enabled for MFA)
Get-MsolUser -All | where {$_.StrongAuthenticationMethods.Count -eq 0 -and $_.UserType -ne ‘Guest’} | Select-Object -Property UserPrincipalName | export-csv non-enabled.csv -noTypeInformation
There is a great script that tells you exactly which type of MFA preference that users have set for themselves (ex: SMS vs Authenticator App). You can download that script from here.
Need Help?
Patriot consulting offers many security services for Office 365 including deploying any of the security solutions you read about in this article. We can also do a full audit of your Office 365 environment and make recommendations to harden the security. We also offer incident response services after you get phished. Contact us at [email protected]