Intune has a new feature called Multi Admin Approval (MAA) which is extremely important to enable because it reduces the risk that an attacker who compromises an Intune Admin can use that privilege to distribute ransomware to all endpoints. A memory trick to always remember this is imagine your sibling shouting “MAAAAA!” when you are doing something wrong. That is like what should happen when an admin account is taken over, goes rogue and tries to distribute ransomware in your environment – someone should be shouting MAA!!! Lol!
You can navigate to this important control here:
https://endpoint.microsoft.com/#view/Microsoft_Intune_DeviceSettings/TenantAdminMenu/~/multiAdminApproval
To create an access policy, your account must be assigned the Intune Service Administrator or Azure Global Administrator role.
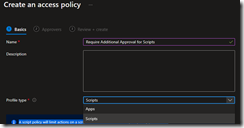
You will need to create two separate access policies, one for Apps and one for Scripts.
Select the group containing the members who can approve requests for create, edit, assign, and delete scripts.
When any Intune admin attempts to create or change a script/app that is protected by an MAA access policy, Intune will queue the request after the user enters a business justification as shown here:
Intune won’t apply the change until a different account explicitly approves it.
Approvers can see the requests in Intune Tenant Admin > Multi Admin Approval
Only administrators who are members of an approval group that’s assigned a protected resource in an access protection policy can approve changes. Approvers can also reject change requests.
This feature is in public preview, but it is pretty awesome!!
To learn more about what happens next, such as what the requestor and approval experience, check out the Microsoft documentation here:
https://learn.microsoft.com/en-us/mem/intune/fundamentals/multi-admin-approval