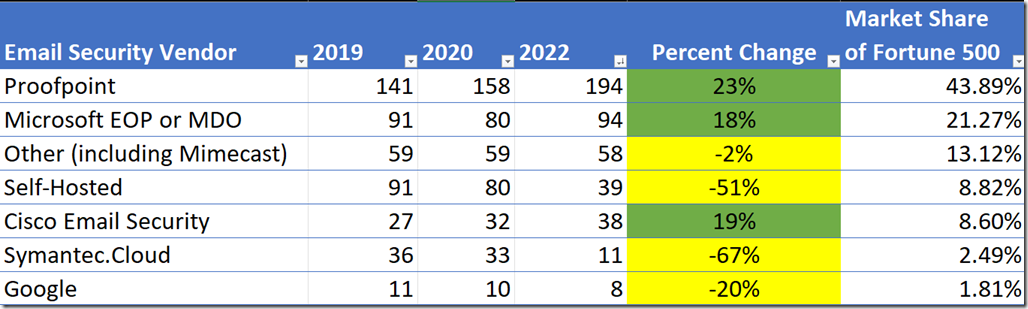
Back in 2019, I wrote a blog post (here) explaining how to identify the primary DNS MX records used by the Fortune 500 and then use that to identify email security vendor market share. Then in 2020, I wrote a post that Microsoft had dipped 12% while others gained.
So when I ran the analysis again today, I was surprised to see that Microsoft had gained 14 new clients since the last time I had run the report two years ago. During that same time ProofPoint and Cisco also gained while Symantec and others lost market share amongst the Fortune 500.
I am asked all the time by customers “Is Microsoft “good enough?” Yes, but you don’t have to take my word for it. Microsoft just received the “AAA Protection Award” from SE labs—a testing lab focused on assessing the efficacy of security solutions. They evaluated email security vendors against a range of real-world email attack scenarios. They found 97 percent of emails that contained threats were blocked. That’s pretty good! Read more about Microsoft’s results here.
At the 2019 Microsoft Ignite Conference, there was a presentation (available on YouTube here) given where Microsoft made a pretty compelling case: since they sit behind other email security vendors (when mailboxes are hosted in Exchange Online) they can see when they could have blocked threats that others missed. In the graphic below, they claim to catch 400% more things than competitors!

MSFT misses 0.002% whereas competitors are missing 0.01% and 0.012% (that is a difference of 400%). To be sure, the competitors will make similar claims since Microsoft is unaware of their unique catch rates.
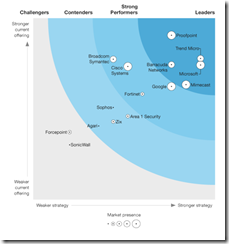
Industry analysts such as Forrester have named Microsoft a leader in email security (read the announcement here)
10 Reasons why I recommend Microsoft for Email Security
There are ten reasons why I recommend Microsoft email security to my clients:
- Automatic signal sharing with Microsoft Defender for Endpoint
- Protect malicious links in SharePoint, OneDrive, Teams, Office on the Web, and Microsoft 365 Apps for Enterprise
- Safe Documents
- Lateral Phishing Protection
- Native Link Rendering
- Anti-Phishing (prevent Business Email Compromise)
- Automatic Investigation and Response
- Threat Explorer
- Threat Hunting & XDR Integration
- Performance
Automatic signal sharing with Microsoft Defender for Endpoint
Whereas most other email security vendors create a silo of malicious file hashes when threats are detonated, Microsoft is able to share this information with Defender for Endpoint within milliseconds because they share a common back-end “the Intelligent Security Graph (PPT Download link).”
Protect malicious links in SharePoint, OneDrive, Teams, Office on the Web, and Microsoft 365 Apps for Enterprise
Whereas other email security products are typically limited to scanning only external emails, Microsoft is able to scan hyperlinks and attachments throughout the productivity applications. This is important because hackers often like to hide their malware in trusted locations such as OneDrive or SharePoint because most organizations cannot afford to block these root URLs since they are also used for business productivity.
Safe Documents
Safe Documents uses the cloud backend of Microsoft Defender for Endpoint (MDE) to scan documents opened in Microsoft Office. Users do not need to have MDE installed for this to work.
License Requirements: M365 E5 Security or full M365 E5. It is not included in the EOP or MDO license plans, you need the E5 Security step-up license (added to M365 E3) or the full M365 E5 suite.
Enable with PowerShell here:
Set-AtpPolicyForO365 -EnableSafeDocs $true –AllowSafeDocsOpen –$false
Learn more about Safe Documents in the Microsoft Documentation (here).
Lateral Phishing Protection
When mailboxes are hosted in Exchange Online, Microsoft is able scan internal emails, whereas other security vendors are usually limited to only when emails are external. Microsoft uses its advantage of hosting the email platform to perform this internal email scanning. This is valuable because if a hacker compromises an account, they will often use that to attack other internal accounts since it will look more trust worthy.
Learn how to configure safe link policies in the Microsoft Documentation (here)
Native Link Rendering

When email security vendors re-write the URL back to their service, they do so because they want to examine the hyperlink at the time of click for threats. Since Microsoft ‘owns’ the Outlook clients (mobile, web, desktop) then they can render the original URL when the user hovers over the link. This is helpful so that the user can use their security awareness training to better judge if the link appears suspicious. Other vendors cannot achieve this since they do not own the most popular email client used in the enterprise.
Read about the announcement of Native Link Rendering back in 2018 (here)
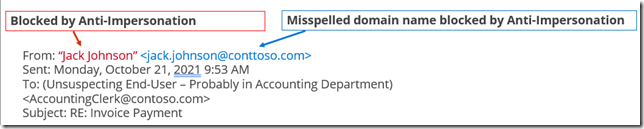
Anti-Impersonation in Anti-Phishing Policy to prevent Business Email Compromise
You can configure anti-impersonation for up to 350 users in a single policy (multiple policies are permitted). The idea is to protect your top executives from having their Display Name impersonated, or domain names that look similar to the domains you own.
Learn more about how to enable Anti-Phishing in the Microsoft Documentation (here)
Automatic Investigation and Response
After a potentially malicious URL click is detected in email, or is manually reported by a User or Admin, or a SOC analyst who integrates AIR with their SIEM uses the Office 365 Management Activity API, then an automated playbook is launched to perform a deep investigation of these 13 steps:
1.Analyze user activity anomalies in Microsoft Cloud App Security, and check the attachment against Defender for Endpoint
2.On-demand check of domain reputation from Microsoft’s ISG and external threat intelligence sources
3.Detect anomalies based on historical mail flow sending patterns for users in your organization
4.Extract indicators from header, body and content of the email for investigation
5.Investigate mail delegation access for user mailboxes related to this investigation
6.Investigate any violations detected by Office 365 Data Loss Prevention (DLP)
7.Detect intra-org and outbound malware or phish originating from users in your organization
8.Investigate any mail forwarding rules for user mailboxes related to this investigation
9.Email cluster analysis based on (1) header, (2) body, (3) content and (4) URLs
10.On-demand check on URL reputation from Microsoft’s ISG and external threat intelligence sources
11.On-demand check of IP reputation from Microsoft’s ISG and external threat intelligence sources
12.Email cluster analysis based on outbound mail flow volume patterns
13.On-demand detonation triggered with Defender for Office 365 for emails, attachments and URLs
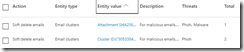
Then an Administrator is presented with an option to soft delete the emails:
Learn more (here).
Threat Explorer
Assuming you have permissions and licensing, you can navigate to Threat Explorer directly here: https://security.microsoft.com/threatexplorer
Threat Explorer is very powerful. You can:
- See malware detected by Microsoft 365 security features
- View phishing URL and click verdict data
- Start an automated investigation and response process from a view in Explorer
- Investigate malicious email, and more
Learn more about Threat Explorer (here).
Also the “Email Entity Page” is also helpful in investigations. Check it out (here). The Microsoft documentation is very good (much better than competitor products).
Threat Hunting & XDR Integration
If you know Kusto Query Language (KQL) then you can construct queries across inboxes, devices, identities, etc. You can also integrate with a SIEM such as Sentinel for true XDR. Sample queries:
- Finds PowerShell activities that occurred right after an email was received from a malicious sender
- Find the first appearance of files sent by a malicious sender among all devices or inboxes
- Find emails containing open redirect URLs, for example:
EmailUrlInfo
| where Url matches regex @”s?\:\/\/(?:www\.)?t\.(?:[\w\-\.]+\/+)+(?:r|redirect)\/?\?”
- Logons to a device after a malicious email was received, for example:
EmailEvents
| where Timestamp > ago(7d)
| where ThreatTypes has_cs “Malware”
| project EmailReceivedTime = Timestamp, Subject, SenderFromAddress, AccountName = tostring(split(RecipientEmailAddress, “@”)[0])
| join (
DeviceLogonEvents
| where Timestamp > ago(7d)
| project LogonTime = Timestamp, AccountName, DeviceName
) on AccountName
| where (LogonTime – EmailReceivedTime) between (0min .. 30min)
Learn more about advanced hunting (here)
Performance
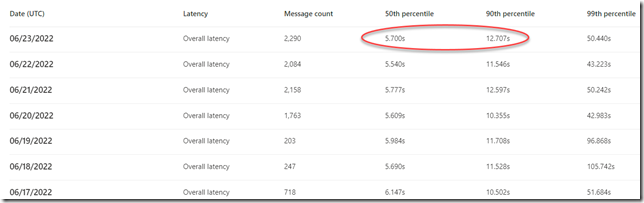
The speed at which Microsoft can detonate attachments is impressive.
Most emails are detonated for threats within 5 to 12 seconds.
Can you imagine what it would take for you to build enough virtual machine capacity in your on-premises network to open every single email attachment received in a separate virtual machine to analyze behavior?
Here is a report you can use to analyze the latency introduced by Microsoft’s email security: https://security.microsoft.com/mailLatencyReport
Try it out
If you are using a 3rd party email security solution, you can begin to evaluate Microsoft Defender for Office now. You will need an E5 Trial subscription and you need to be a member of the Security Administrator and Exchange Administrator roles to set up the evaluation.
Learn more here: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/try-microsoft-defender-for-office-365?view=o365-worldwide
Make the switch!
Already convinced? You can plan to make the switch from a 3rd party email security vendor to Microsoft by following the excellent documentation (here) or contacting a Microsoft Partner (such as Patriot! (My company!) – contact us at [email protected] for a quote!).