My first attempt at Windows 365 Business failed with error message “Setup failed, please reset your Cloud PC.” I thought it would be as simple as assigning a license to a user.
Turns out there are a few additional configuration prerequisites that must take place.
The key is to understand that during the provisioning process, a new user account named CloudBPRT or “Windows 365 BPRT Permanent User” is created in Azure AD. This account is used to join the machine to Azure AD.
1. If you have a conditional access policy that requires MFA then you need to exclude the CloudBPRT user from the policy.
A great troubleshooting tip is to use the WhatIf tool and add the CloudBPRT user to see which CA policies are applying to the user and then exclude the user from these policies

2. In Device Settings you must disable the requirement to require MFA when doing Azure AD Join, and If you limit which users or groups can join Azure AD, you must add the CloudBPRT user (as shown below)
3. The CloudBPRT user must be assigned an Intune license if you are doing Intune Auto Enrollment
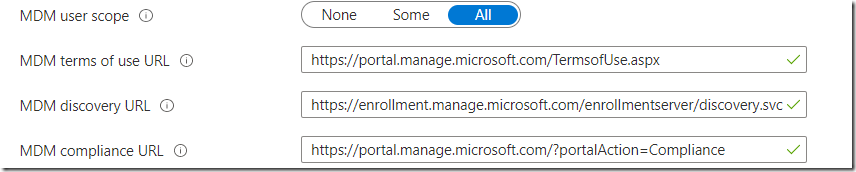
4. If you Configure MDM AutoEnrollment, you must make sure the CloudBPRT user is a member of the scope, or that it is set to ALL as shown below
6. In my experience, after Cloud PC was reset, I also had to select Restart before I was able to logon, otherwise I got a blank screen when trying to connect to Cloud PC.
Reference: Windows 365 for Business Troubleshooting Documentation
Other tips:
- The device will automatically enroll into Intune as an Autopilot device, but there is no need to configure an Autopilot Enrollment Status Page, nor can you target an ESP to Cloud PC’s per Microsoft Documentation (here)
- The device may fail compliance checks since bitlocker is not supported on Cloud PC’s, so it will be necessary to create an Intune Filter for “Cloud PC” and exclude that from policies that require Bitlocker while requiring that filter for other settings so that you can pass conditional access policy checks. For instructions on how to create an Intune filter click (here)
- It can take several hours for Microsoft Defender for Endpoint to perform the initial sync of the risk level to Intune Compliance, so if your Intune Compliance Policy has the setting “Require the device to be at or under the machine risk score” then be prepared to adjust your “mark device as non compliant’ to have some grace period such as a day otherwise your new employee will be locked out after their first sign-in.
“Once the connection is established, the services are expected to sync with each other at least once every 24 hours.” (reference here)



